
Many of us are uncomfortable with having our valuable data stored somewhere in 'the Cloud'.
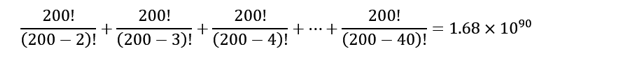
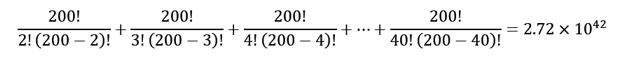

CloudCORA.com is owned and operated by CORA Cyber Security Inc. (CORAcsi), a Canadian Corporation operating out of Windsor, Ontario Canada.
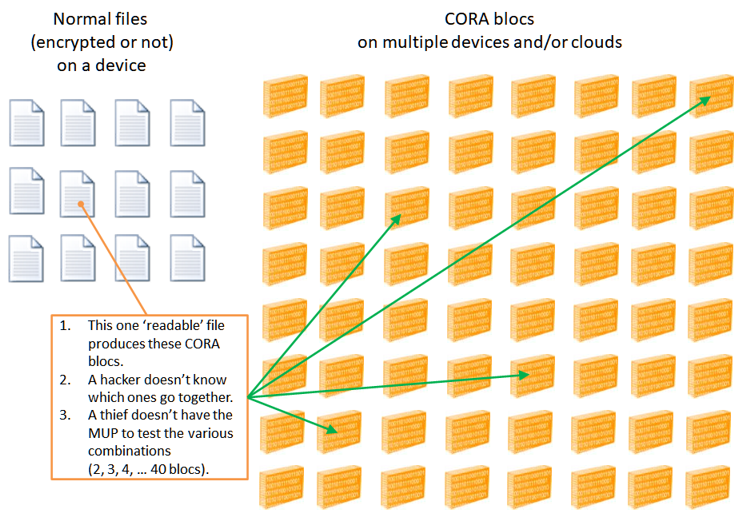
This why, if CORA is used properly, it is an unbreakable solution!
CORA-X lite is standalone program that can be installed on your computer and will lock/unlock your files/folders. It is secure and available free of charge from the Microsoft Store.
At this time, CORA-X requires Windows 10 or later.
The main advantages to using CloudCORA subscriptions are:
Originally CORA was designed and developed as a sole proprietorship named pieV.com. The author of CORA who is the Director and President of CORAcsi has enjoyed a vast array of professional experiences spanning Physics, law enforcement and teaching.
"CORA began in 2008 as a desire and inspiration to protect Mr. Latouf's personal data and software in a manner that was superior to encryption, which has been known for over a decade to be limited and breakable."
Mr. Latouf's fascination with data-security began with prime numbers and a prime number generator.
Recently the global community has discovered that factorization-based encryption will be antiquated by quantum computers.
CORA is a step beyond encryption because: